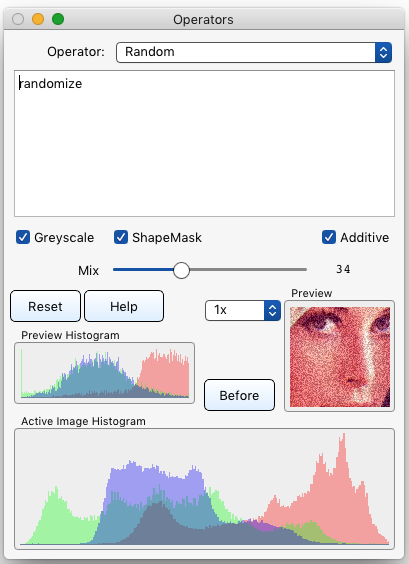
§ 12.11.72 - Random
Scripting command: random [Monochrome=0...1] [Shapemask=0...1] [Additive=0...1] [Amount=0...100] [Key=word(s)]
Fills areas with pseudo-random values based on a key (a text string) you supply. Can generate color or greyscale pseudo-random data, and can add pseudo-random dither to an image when ✓ ShapeMask and ✓ Additive are both checked. In that case, Amount ![]() will set the intensity of the dither.
will set the intensity of the dither.
If the key is simply the word randomize then each generation will be different from the last and not reproducible. To create a reproducible pattern, use a keyword string other than that specific word.
An example of an encryption technique:
- Promote the image into a layered image
- Clone the layer using clone in the Layers dialog
- Set the layer mode of the clone to XOR
- Select the "entire image" area tool
- Select the Random operator
- Choose a long, highly variable passphrase
- Click on the clone image (the top layer)
That's it. The master is now an encrypted version of the image. You can now save the master as an 64-bit .ato file using S (shift+s); the only way to get it back from that .ato file is to repeat the process: load it back in, begin with step one above, and make sure you provide the same key or the image will not decrypt.
This is good where only you know the key. However, if you send the image to someone else, and they don't know the key, you also have to send them the key, and at that point, the encryption is insecure. To get around this, you can use the "double locked box" technique. It works like this:
- You encrypt the image as described above. Send the image to the other party.
- They encrypt the already-encrypted image again, using their own unique key. They then send this doubly-encrypted image back to you.
- You now decrypt the image using your own key. This will result in an image that is only encrypted using the other party's key. You send this image back to the other party.
- The other party now decrypts the image using their key, and it will decrypt completely.
Using this approach there is no exchange of keys between the two of you, only encrypted information, and no intermediate party can steal the keys in transit, which makes the technique secure with regard to channel-based interception.
For extra encryption goodness, generate more than one one layer of pseudo-random information, each with its own unique key. Each layer goes above the image to be encrypted; each layer is set to XOR mode. To decrypt the image, all the layers will have to be reproduced with the correct keys. Don't lose the keys!
, Previous Page . Next Page
t TOC i Index k Keyboard o Operators g Glossary c Changes
| Please consider supporting my iToolBox development efforts with a small PayPal donation. |